
Testing Terraform Code – Part One: A Deep Dive into Static Analysis Tools
Testing Terraform Code – Part One: A Deep Dive into Static Analysis Tools
30 January 2024
Jonathan Bernaerts

Key takeaways
- Don’t forget to use Git correctly as a first line of defence.
- Tfsec is an easy-to-use tool that focuses on security checks.
- Terrascan checks for both security and compliance but is more difficult to use.
- Driftctl is a great niche tool for detecting infrastructure drift but is in maintenance mode.
In application development, automated tests often stop at the application level. But what if we could push the boundaries and extend this to the very foundation of our applications – the infrastructure level?
In this two-part blog series, we will discuss various tools available for infrastructure testing, focusing on Terraform, a popular Infrastructure as Code (IaC) tool. In this first part, we will discuss three tools that excel in static analysis: tfsec, Terrascan, and driftctl.
First Things First: The Art of Using Git
Before we start our overview of static analysis tools, let’s focus on the basics. Git is more than just a version control system; it’s a powerful tool that, when used correctly, can provide a robust first line of defence.
Running a Terraform plan when creating a pull request also allows us to evaluate more than just the code itself. It gives us a glimpse into the potential impact of our changes on the infrastructure.
Pull requests can sometimes be accepted too quickly, so it’s crucial to review each other’s code. By dedicating time to thoroughly reviewing code and using the four-eyes principle, we can make sure that our code is not just functional, but also secure and efficient.
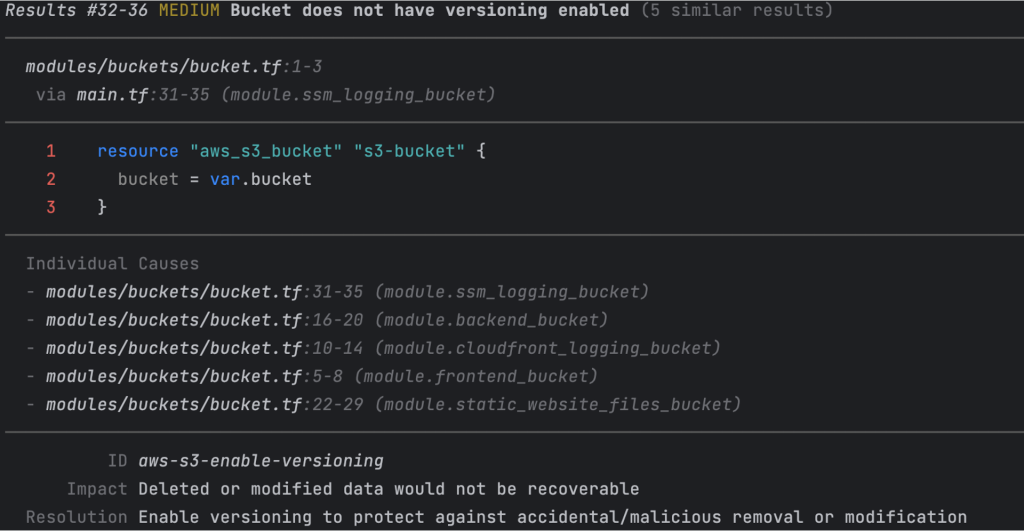
Tfsec: The Security Sentinel
tfsec is a static analysis tool (now part of the overarching Trivy solution) with a focus on security checks that constantly scans your Terraform code for potential security vulnerabilities. It is basically a dataset full of rules for code, like naming your objects according to certain rules.
Of course, some of the default rules make no sense in some cases. To solve this, we can ignore checks by adding the following line above the resource or module block.
#tfsec:ignore:<RULE_ID>
Resource "" "" {}
#or
#tfsec:ignore:<RULE_ID> tfsec:ignore:<RULE_ID>
Module "" "" {}
Tfsec features a high degree of customisability, letting you alter just about everything you want. You can create a config file to exclude rules, edit the severity of checks, and add your own checks formatted in JSON or YAML, like in this example.
--- exclude: - aws-ec2-add-description-to-security-group-rule severity_overrides: aws-ssm-secret-use-customer-key: HIGH custom_rules: .tfsec/ec2_tag_name_tfchecks.json
It also runs great in your CI/CD pipeline, including the option to add comments on pull requests. If you want to try out tfsec’s many possibilities, you’ll be happy to know that it also has some great documentation available.
Pros:
- Simplicity: tfsec is straightforward to set up and use.
- Custom Rules: It lets you define specific security checks and compliance requirements.
- Active Community: it receives regular updates and improvements.
Cons:
- Narrower Focus: tfsec primarily concentrates on security checks, which may require additional tools or processes for comprehensive compliance scanning.
- Limited Built-in Policies: While it provides essential security checks, some organisations may need to invest more time in defining custom policies for specific compliance requirements.
Terrascan: The Compliance Crusader
Terrascan is designed for security and compliance scanning of Terraform configurations and infrastructure code, making sure that it aligns with best practices and meets compliance requirements.
Terrascan is similar to tfsec, but less flexible to customise. Customising its rules requires frequent references to documentation, because you’ll have to search for the descriptions of specific rules if you want to ignore them. There are also multiple sources where you can get Terrascan and, depending on your source, features might work differently or just be unavailable.
Compare this to just adding a single line of code in tfsec, as we’ve shown above, and you’ll understand why getting your setup right with Terrascan can be a frustrating experience.
Pros:
- Comprehensive Focus: Terrascan covers both security and compliance checks.
- Customizability: It supports custom policies and can be extended with custom checks… but these can be difficult to set up.
- Active Community: Like tfsec, Terrascan has an active community that shares knowledge and documentation.
Cons:
- Complexity: The comprehensive range of checks and policies may be overwhelming and/or require additional configuration.
- Learning Curve: Extending Terrascan with custom checks takes time and practice.
Driftctl: The Drift Detective
Unlike tfsec and Terrascan, driftctl has a more niche use case: tracking and managing infrastructure drift. It’s constantly on the lookout for discrepancies between your Terraform state file and the actual state of your deployed infrastructure by checking with your cloud provider.
This also lets you check the usage of your IaC tools by showing you a coverage percentage. A low number might indicate that your account has different environments, your IaC is split up in different state files, or there are a few resources that have been created manually.
However, there is one big catch: the project’s GitHub repository mentions that it is currently in maintenance mode. New contributions may not be reviewed or integrated, posing potential security risks. It’s still worth using for its niche use case, but you should definitely use at least one other tool to check your code’s security.
Pros:
- Drift Detection: driftctl excels in identifying and managing infrastructure drift.
- Detailed Reports: The tool generates detailed reports of the differences found, making it easier to understand and address the drift.
Cons:
- Specific Focus: driftctl’s specific focus on drift detection requires additional tools for comprehensive security and compliance scanning.
- Maintenance Mode: driftctl’s GitHub repository is currently in maintenance mode, leading to potential security risks if not paired with other tools.
Conclusion
Each of these tools brings unique strengths to the table. tfsec shines in its simplicity and focus on security, Terrascan offers comprehensive security and compliance scanning, and driftctl excels in detecting and managing infrastructure drift. The choice between these tools depends on your specific needs and the challenges you face in managing your Terraform infrastructure.
Stay tuned for part two of our Terraform testing blog series, where we’ll compare two tools for unit and integration testing: Terratest and Terraform Test.
Need some help figuring out the latest Terraform tools, or have some other DevOps-related questions? Don’t hesitate to contact us, we’ll gladly help you out!

Sorry, the comment form is closed at this time.